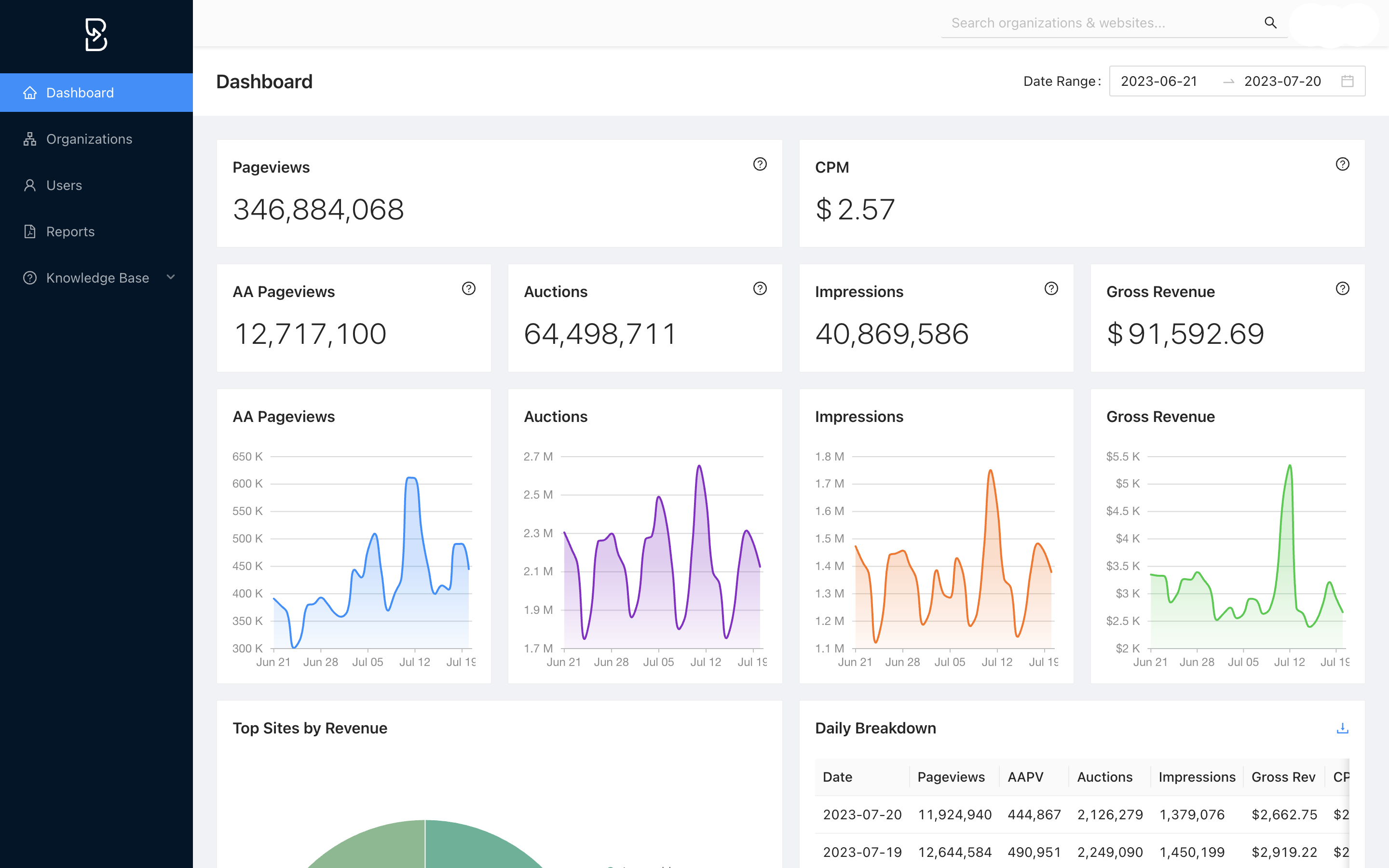
Better ads for your users, more revenue for you.
Using award-winning programmatic technology, Blockthrough helps the world’s leading publishers grow their revenue by delivering a lighter ad experience to 250 million users across the Web.
Trusted by publishers all over the world





Still fighting your adblock users?
Publishers lose billions to adblocking each year. At the same time, most adblock users don’t hate advertising—they simply want a safer, less interruptive experience. We enable publishers to cater to these users, without badgering them to turn off their adblocker.
- Official Google MCM Partner
- IAB EU TCF v2.0 certified vendor
- Free adblock analytics suite
- No setup fee, upfront cost or commitment



Measure adblock rate across your sites
Confidently measure the percentage of your visitors who use adblocking tools—including the subset that’s already opted-in to receive a lighter advertising experience.
Seamlessly restore your ad stack
Leverage your existing direct demand partnerships, connected SSPs, and ad server. Our tech handles creative filtering and compliance. No development work needed.
Delight users with a light ad experience
We ensure that all ads served meet leading ad quality standards including Acceptable Ads and Better Ads. Delight your users with the high-quality experience that they expect.
Drive incremental revenue growth
Generate a predictable stream of incremental revenue that grows with your audience, allowing you to get one step closer to realizing the full potential of your inventory.
Key product features and benefits at a glance
Single-line integration
Just add one line of JS code to your website header to get started. Our technology plugs into your ad server or header bidding wrapper and acts as a filtering layer for ad quality compliance.
Plug-and-play demand
Easily restore all compliant bids from your existing demand sources and line items, including direct and sponsorship, programmatic, house, native, Google AdSense, Google AdX, and Amazon.
Grow ARPUs and Page RPM
By surfacing your hidden audience and making it addressable, Blockthrough helps increase average revenue per user, Page RPM, and other key revenue performance metrics across the board.
Custom report builder
Discover BT Exchange
Blockthrough brings in premium demand via our direct seats with top-tier SSPs and competes against your existing line items on price priority. Connect via client-side, server-side, or Open Bidding integration.
Alternative monetization
We recommend Acceptable Ads as the primary solution for publishers. However, we also provide products to monetize adblock users who are not opted-in, including a whitelist wall and donation widget, to maximise revenue.
>10,000
Sites powered by Blockthrough’s technology across the globe
3 Billion
Adblock pageviews monetized
each month with compliant ads
$120M+
Total revenue recovered for our publishing partners to-date
13
Awards for innovation, growth, and contribution to the ecosystem
The gone fishin'
solution to ad blocking.
*Fishing gear and loving pet not included


Steve Mummey
"We tested a handful of solutions, including a message wall approach, before we ultimately decided to go with Blockthrough for the team and their thoughtful approach to both revenue and user experience."

Paul Bannister
"We're generating over $100k a month with Blockthrough's solution. This is revenue that goes back into powering the creator economy, that—in turn—powers the web and keeps it open and freely accessible.”

Chris Acosta
"Prior to Blockthrough, Healthline worked with another vendor that had a convoluted process of recovering ads with less than stellar account management. Blockthrough has responsive white-glove service for us."

Matt Burgess
"Freestar is thrilled with the results we have achieved from our partnership with Blockthrough. The implementation is ultra turnkey, light on the page, and allows us to recover significant levels of ad blocked revenue."

Cody Bye
"We experimented with building our own Acceptable Ads filtering technology but it just proved to be way too cumbersome and the amount of revenue lift we observed was lower than what we wanted."
Blockthrough is the most popular ad-filtering solution among the Comscore Top 150. Explore our case studies to learn how we help publishers strike the perfect balance between revenue and UX.
Latest updates from our blog
How Blockthrough reclaimed 10 billion pageviews for Venatus
2023 eyeo Ad-Filtering Report
Top 10 digital publishing trends for 2024
INDUSTRY RECOGNITION
FOR BLOCKTHROUGH




